Why People Need a New Online Personality?
There are several reasons why one might need a new online personality.
The Internet could be a more safe place. Every time you go online, there are particular security and privacy risks. And the fact is most people are not even aware of them.
If you want to maintain privacy or anonymity when you surf the Internet, there are several ways to do so.
 |
| The Best Way to Remain Anonymous Online: eAskme |
Below are a few reasons why you should get a new online personality:
- Maintain anonymity and privacy on the Internet.
- Separate your personal and professional online presence
- Eliminate personal harassment or negative online experiences
- Prevent identity theft
- Participate in forums and communities without being judged.

New account instead of banned:
If you use multiple accounts on the same platform, they may detect it easily via your IP address or browser fingerprints and ban you.
Once banned, you won't be able to log into your account on the particular platform or use it. And worst of all, you'll lose everything you built with that profile.
Managing multiple accounts on a platform from a single web browser is the most significant mistake people make.
Let's say you are a multiple clients' brand manager or a social media manager. So you will be required to log into their social profiles and juggle between them.
If you use a regular web browser, it's going to be painful, and eventually, you will be banned all the same.
Browsers for multi-accounting like Octo Browser help you with multi-accounting for business reputation management.
One can install, set up and configure multiple profiles using Octo Browser. Each profile is for a separate social media profile or affiliate account.
Since each of these profiles will have an entirely different system fingerprint, the platform will not detect that they are being run from the same physical device.
You can set up and configure everything like IP address, screen resolution, device hardware info, connection info, and much more.
This way, it becomes impossible for anyone to find your real identity online, and you can flawlessly manage multiple accounts without being banned.
How can a website recognize you?
There are several ways a website can recognize you the next time you visit it.
Cookies, IP addresses, user agents, fingerprinting, etc., are a few ways a website can detect you.
Hardware and Software Info:
Many websites collect information about your device and software to create your device fingerprint.
It will include screen resolution, hardware info, IP address, user agent, and more. It makes it easy for websites to track you.
Cookies:
Every time you visit a website, a small cookie is stored in your web browser. This cookie is a small text file with your account preferences and login information.
The next time you visit the website, it looks for the cookie; if found, it can easily understand it's you.
IP Address:
Every device connected to the Internet will have a unique identification address called an IP Address.
Every time you visit a website, your IP address is logged. So the next you visit the website, they can recognize you by your device IP address.
What is an IP Address, and how does it work?
An IP (Internet Protocol) address is a unique numerical value assigned to every device connected to the Internet.
The IP address makes it easy to transfer data packets to and from connected devices. It helps route the data packets to the correct destination device.
Since it is a unique value, no two devices can have the same IP address.
IPv4 (32-bit) and IPv6 (128-bit) are two types of IP addresses. An IP address can be broken down into two parts. The first is the network part, and the other is the host part.
The network identifies the network, and the host part identifies the host on the said network.
Every time you visit a website, your device's IP address will be in the server log. This way, the website can know that a person with a particular IP address visited the site.
The IP address will let them know from which country you are visiting their site.
What is Digital Fingerprint?
A digital fingerprint is a unique set of values or characteristics which can be used to find a particular person or device on the Internet.
The digital fingerprint is a collection of various data:
- Web browser
- Type of operating system
- Screen resolution
- Fonts
- Plugins
- Network
- Device hardware
- IP address
- MAC Address
- And other attributes
Digital Fingerprints are generally used for tracking a user for advertising and marketing needs.
As digital fingerprints include both software and hardware information, it becomes easy to track a user's online behavior and preferences.
A digital fingerprint changes when a piece of new information is added, like a different preference set by the user.
Octo Browser allows users to spoof digital fingerprints by setting custom values of their choice.
This way, you can create multiple profiles with entirely different but actual digital fingerprints and surf the Internet.
Deep hardware fingerprint tweaking is done using specific technologies, such as WebGL, Canvas, and WebRTC.
WebGL:
WebGL allows browsers to render 3D graphics on the web and gives away a bunch of data about the visitor's device, such as the GPU and its driver version.
Canvas:
Canvas allows web browsers to render 2D graphics and images dynamically. It can be used to learn information about screen resolution and color depth.
WebRTC:
WebRTC enables real-time communication in web browsers, like voice and video calls within Web browsers; since it has access to a host of data, it reveals information about the user's device, like the IP address and system information.
What can you do in case you need a new online personality?
There are several ways one can obtain a new online personality.
It includes options like using a VPN or a proxy server, using dedicated multi-accounting web browsers like Octo Browser, using an entirely new system with an entirely new system configuration and email, having multiple emails and mobile numbers, etc.
Hiding your IP with a proxy or a VPN: how does it work, and what's the difference?
There are several ways to hide your IP address. The first uses a VPN, and the second uses a proxy server.
VPN, aka virtual private network, works by encrypting all of your traffic and routing it through a server handled by the VPN company.
Every time you connect to a VPN, you can select a server of your choice. For example, if you are in the United States, you may select any other server like Germany or India.
Now that you have enabled a VPN, the sites you visit or other online services will see your VPN server IP address.
This way, you have hidden your original IP address. The website you visit or the services you use won't be able to track your actual IP address since your traffic through the VPN server is encrypted. A VPN provides a higher level of security and privacy compared to a proxy server.
A Proxy Server acts as an intermediary between you and the Internet. It routes all the requests and responses through a proxy server instead of a direct connection to the Internet.
When a proxy server is used, the IP address visible to the websites you visit is that of the proxy server, thus hiding your original one.
Regarding security and privacy, a VPN is recommended over a proxy server.
Using an Antidetect Multi-accounting Browser for business reasons. How does it work?
An anti-detect multi-accounting browser is a particular web browser designed to help users create and manage multiple online identities, known as multi-accounting.
A browser for multi-accounting uses an array of techniques to obscure and alter the information transmitted by the users' devices.
Websites visited using anti-detect and multi-accounting browsers like Octo Browser will only see the altered information, thus hiding the original device info.
Generally, a multi-accounting web browser will change or hide the information like the IP address, browser fingerprint, user agent, device info, location, network info, and more.
This helps users to maintain separate and distinct online personas easily.
Antidetect multi-accounting browsers are used for various reasons, including business ones such as social media management, multi-client account management, market research, competitor analysis, and account creation for multiple brands or businesses.
How to get the required level of anonymity? Octo Browser + proxy use case
Achieving a high level of anonymity online requires careful consideration of multiple factors. Octo Bowser is the go-to choice for multi-accounting.
Using a proxy and an anti-detect web browser helps increase the chances of creating a trusted online account with multiple layers of protection.
A proxy server helps you easily hide your IP address and change location.
On the other hand, Octo Browser obscures and alters various characteristics of your device and browser, such as fingerprint, user agent, and more, to help you stay truly anonymous on the Internet.
Using a proxy server and anti-detect software, you can create a more comprehensive online persona that is less likely to be detected by websites and online platforms.
Let's see how to use Octo Browser and a proxy together to get the required level of anonymity when surfing the web.
Firstly, you need to head to the Octo Browser's website and download the browser for your device. It is available for Windows, macOS, and Linux.
You should have a valid Octo Browser subscription to use the browser.

Once installed, you must log into your Octo Browser account to begin the process.
Click the Proxies option to configure and set up proxies in the web browser.
Hit the Add Proxy button to add a new proxy, or click the Bulk Add option to add multiple proxies in a single click.

In the pop-up, you need to enter information like the Title, type, host, port, username, password, and a URL to change the IP.
Once you enter every detail, you need to click the Check Proxy button to ensure it's working correctly.
Now that you have set up the proxy, the next step is to use it with a profile in Octo Browser.
Switch to the Profiles tab.
Click the Create Profile or Quick Profile button to create a new profile with your desired settings.
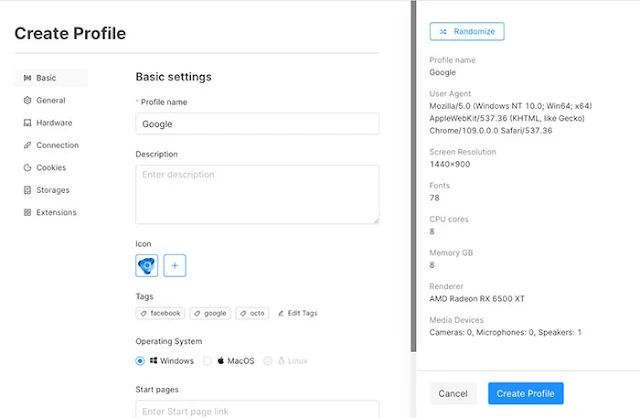
Once created, click the Direct option under proxy to specify which proxy to use.

Select the proxy you added just now in the pop-up by expanding the drop-down menu and selecting it.

Once the proxy is selected, click the Start button and wait for it to open the browser window.
Voila! You have successfully configured a proxy server in Octo Browser. Now you can surf the Internet the way you would typically do.
Octo Browser + VPN use case:
Using a VPN is even easier. You need to use your favorite VPN service and change your IP and location to do this.
After that, you must select or create a profile in Octo Browser and click "Start."
Conclusion:
Why do you need to stay anonymous?
There are several reasons why someone may need to stay anonymous online.
For example, they may wish to protect their privacy, maintain two different profiles for work and personal life, avoid website tracking, and more.
How can you be recognized on the Internet?
One can be recognized on the Internet using several factors like the IP address, fingerprint, device and software info, online behavior pattern, cookie files, and more.
How to hide your IP address?
One may use a VPN or a proxy server to hide the original IP address.
The traffic is tunneled through a VPN or a proxy server when either is used, hiding your actual IP address and location.
How to spoof your digital fingerprint?
The best way to spoof your digital fingerprint is using a multi-accounting anti-detect browser like Octo Browser.
It helps you change and alter the online representation of your device's and browser's fundamental characteristics.
It changes parameters like the IP address, user agent, time zone, screen resolution, and more.
How to get the optimal level of anonymity?
Pairing a proxy or a VPN with Octo Browser helps you attain optimal anonymity on the Internet. A proxy helps you to tunnel your traffic through a different server and hide the original IP address and location.
In contrast, Octo Browser helps you to spoof your device fingerprint and give you a new online persona.
If you still have any question, feel free to ask me via comments.
If you find this article interesting, don’t forget to share it on Facebook, or Twitter with your friends and family.
Don't forget to like us FB and join the eAskme newsletter to stay tuned with us.




























